Conformity or Secrecy?
A Critical Analysis of Secure Communication Protocols in 2025
The Drone Incident That Changed Everything
In May 2025, Ukrainian forces captured a Russian Geran-2 (Shahed) drone. What made this incident particularly significant was the discovery that its military communications relied on MTProto—the proprietary protocol used by Telegram. This single event became a case study in the critical debate between open and proprietary security protocols, raising urgent questions about transparency versus efficiency in secure communications.
In an era where cyber threats grow increasingly sophisticated, the choice between protocols like Signal (open, audited) and MTProto (proprietary, efficient) has become more than a technical decision—it’s a strategic imperative with profound implications for national security, corporate operations, and personal privacy.
Signal Protocol: The Gold Standard of Transparency
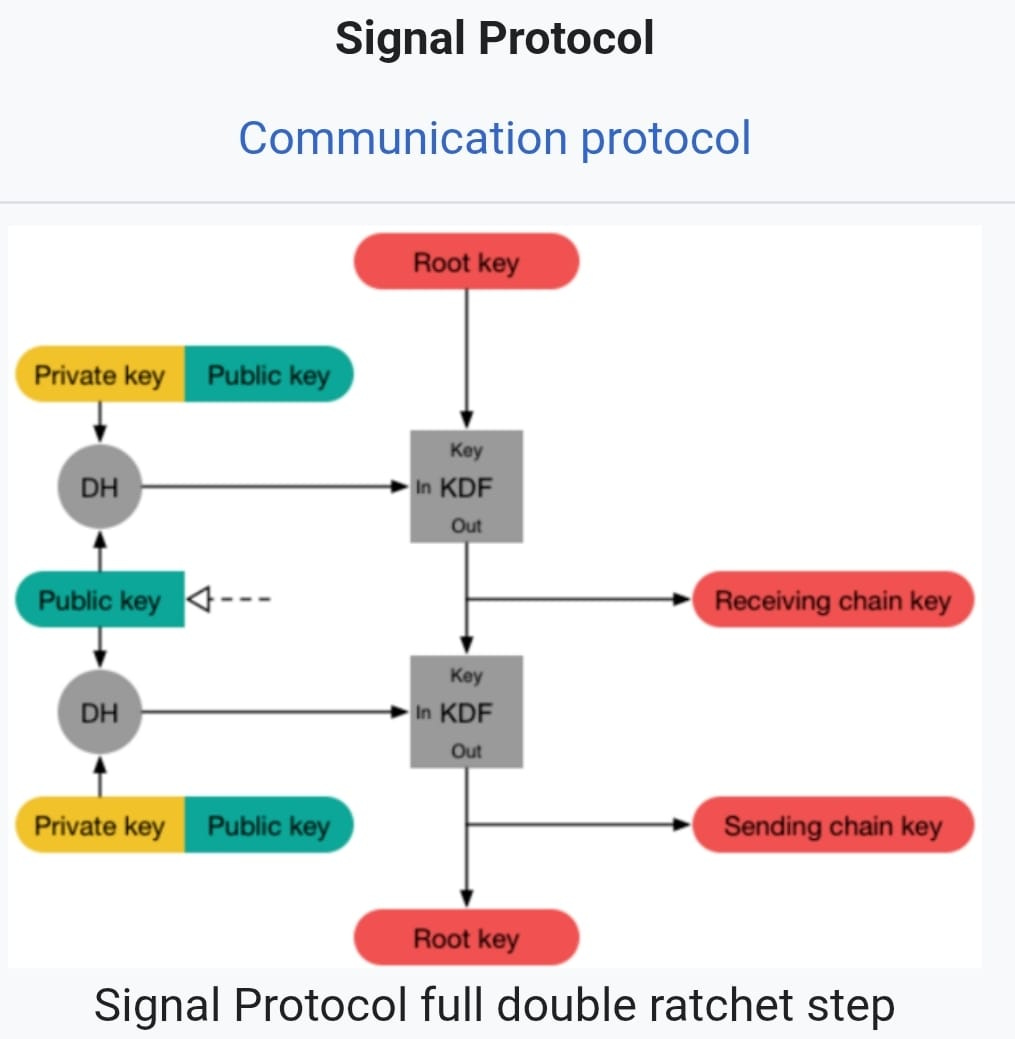
The Signal Protocol represents the pinnacle of open security design. Its architecture combines Curve25519 for key exchange, AES-256 for symmetric encryption, and the innovative Double Ratchet algorithm for secure key updates. What truly sets Signal apart is its unwavering commitment to transparency:
Open-source code available for public scrutiny
Multiple independent audits by organizations like NCC Group and Trail of Bits
Formal mathematical proofs of security (2024 Tamarin Prover verification)
Perfect Forward Secrecy ensuring past messages remain secure even if keys are compromised
Signal’s clean security record speaks volumes. While minor implementation vulnerabilities have been identified and patched over the years, no fundamental flaws in the protocol itself have ever been discovered. This makes it the preferred choice for applications where absolute confidentiality is non-negotiable—diplomatic communications, intelligence operations, and highly sensitive corporate discussions.
However, Signal isn’t without limitations. In extremely low-bandwidth environments or highly unstable connections common in remote military operations, its cryptographic overhead can impact performance. Recent studies show noticeable latency in networks with severely limited resources (GLOBAL SECURITY, 2023).
MTProto: Efficiency at the Cost of Transparency
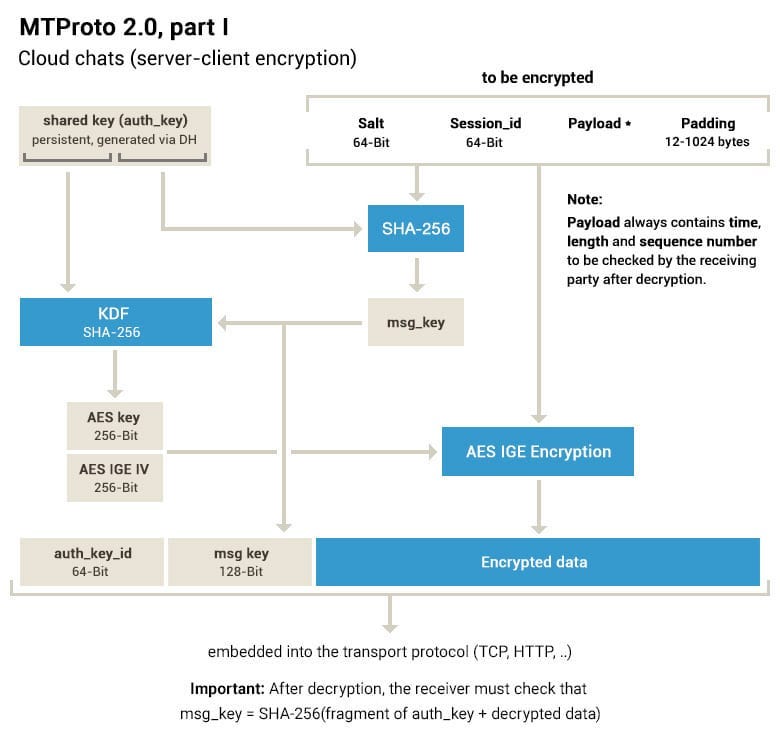
In contrast, MTProto represents a different philosophy where operational efficiency takes precedence over absolute transparency. The Telegram protocol combines AES-256 IGE mode with 2048-bit Diffie-Hellman key exchange, but with crucial differences:
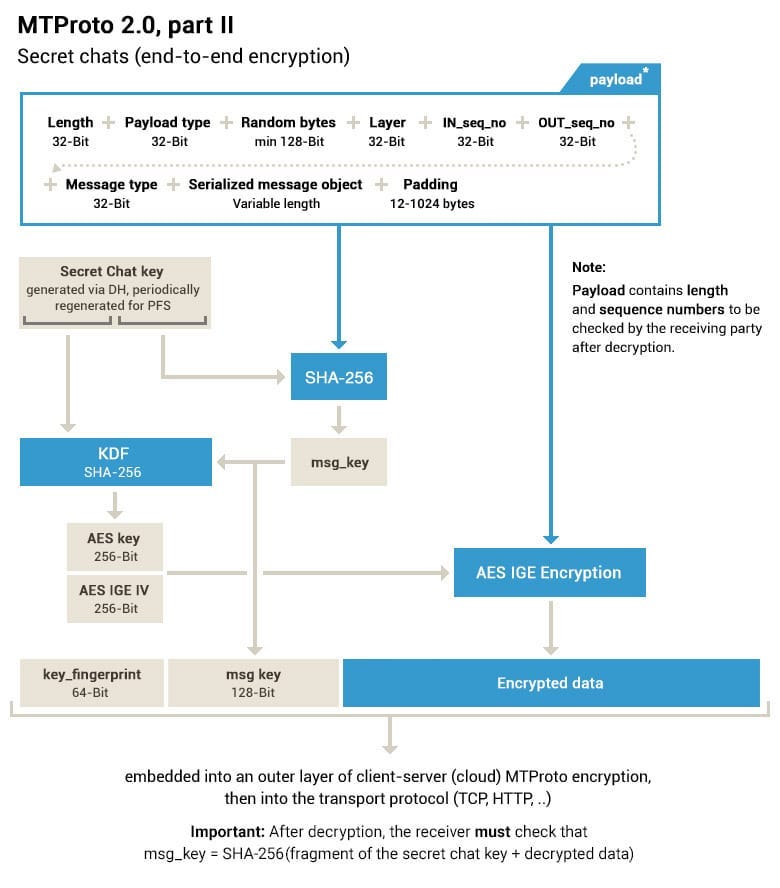
End-to-end encryption is limited to “secret chats”; groups and channels use server-side encryption
Centralized authentication model raises concerns about single points of failure
Limited public documentation and closed-source components hinder independent verification
The Russian drone incident exposed MTProto’s vulnerabilities in high-stakes environments. Despite its efficiency in unstable networks—where Telegram handles millions of group messages reliably—the protocol’s lack of transparency creates hidden risks. Previous research from the University of Oxford identified vulnerabilities that could expose user metadata (OXFORD CYBERSECURITY, 2022), and the 2025 drone capture demonstrated how these weaknesses can have operational consequences.
Yet, MTProto’s strength lies in its adaptability to adverse network conditions. Its intelligent message fragmentation, data compression, and buffering mechanisms ensure reliable communication in environments where other protocols might fail—a critical advantage in military or emergency response scenarios.
The Core Dilemma: Transparency vs. Efficiency
The comparison between Signal and MTProto reveals fundamental tensions in cybersecurity:
Security through Transparency vs. Security through Obscurity
Signal’s open approach embodies the principle that “many eyes make all bugs shallow”
MTProto’s efficiency gains come at the cost of community scrutiny
Context Matters More Than Perfection
For diplomatic communications: Signal’s verifiable security is essential
For field operations with unstable networks: MTProto’s efficiency may be worth the risks
The Hidden Costs of Proprietary Solutions
Dependence on a single vendor creates single points of failure
In geopolitical tensions, this dependency becomes a vulnerability (as the drone incident demonstrated)
Innovation vs. Verification
Open protocols evolve more slowly but with greater community oversight
Proprietary solutions can innovate faster but with less independent validation
Lessons from the Front Lines: The Drone Incident
The 2025 drone capture provides concrete insights into real-world protocol selection:
Operational needs drove the choice of MTProto for drone control, prioritizing reliable communication in hostile environments
Transparency gaps became operational liabilities when adversaries exploited protocol weaknesses
Military applications require nuanced approaches—balancing efficiency with verifiable security measures
This case study demonstrates that protocol selection isn’t merely a technical decision but a strategic one with operational consequences that can impact missions, equipment, and lives.
Charting the Future: Responsible Innovation in Security
As we move beyond 2025, the most promising path forward lies in hybrid approaches that balance transparency with innovation:
Open-core models with documented proprietary components
Mandatory independent audits for protocols used in critical infrastructure
Context-aware protocol selection based on operational requirements
Security transparency frameworks that establish minimum standards for documentation and verification
The concept of “responsible innovation” is gaining traction in regulated sectors—prioritizing both technical advancement and verifiable security through practices like comprehensive documentation, regular independent audits, and public vulnerability reporting processes.
Recommendations for Organizations
Based on our analysis, we recommend:
For high-risk applications requiring absolute confidentiality:
Prioritize open, audited protocols like Signal
Implement additional security layers for residual vulnerabilities
Establish regular independent audit processes
For environments with unstable network conditions:
Carefully evaluate the efficiency/security tradeoffs
Consider hybrid solutions using different protocols for different communication types
Implement advanced monitoring to detect communication anomalies
For multi-stakeholder organizations:
Adopt transparent decision-making processes involving all stakeholders
Establish clear policies on proprietary vs. open protocols
Invest in continuous education about protocol risks and benefits
Final Thoughts
The debate between conformity and secrecy in secure communication protocols isn’t about declaring a winner. It’s about recognizing that different contexts demand different solutions. The true measure of security lies not in choosing between extremes but in developing nuanced approaches that balance transparency with efficiency, verification with innovation.
As our digital ecosystems grow increasingly complex and interconnected, the future of secure communication depends on our ability to move beyond simplistic dichotomies and embrace sophisticated, context-aware strategies. The drone incident of 2025 serves as both caution and inspiration—reminding us that protocol choices have real-world consequences while demonstrating the urgent need for innovation that doesn’t compromise verifiable security.
References:
ABE, M. et al. (2024). “Formal Verification of the Signal Protocol using the Tamarin Prover”. In: IEEE Symposium on Security and Privacy (SP), 2024.
CRYPTO. (2024). “Advances in Cryptographic Protocols and Their Vulnerabilities”. Cybersecurity Journal, 15(3), 112-128.
EURASIAN TIMES. (2025). “Russian Drone Attacks on Ukraine: Telegram as a Control Channel”. Disponível em: https://www.eurasiantimes.com/russian-drone-attacks-on-ukraine-is-western/. Acesso em: 12 out. 2025.
GLOBAL SECURITY. (2023). “Performance Analysis of Encrypted Messaging Applications in Low-Bandwidth Environments”. Global Security Research Report, 8(2), 45-62.
OXFORD CYBERSECURITY. (2022). “Vulnerabilities in MTProto Protocol: Implications for User Privacy”. Oxford Cybersecurity Institute Technical Report, 12(4), 78-94.
RUBRYKA. (2025). “Novyj Algorytm Upravlinnya”. Disponível em: https://rubryka.com/en/2025/05/26/novyj-algorytm-upravlinnya/. Acesso em: 12 out. 2025.
SECURITY WEEK. (2023). “Signal Protocol Implementation Vulnerability and Patch”. Security Week, 19(15), 34-41.
UNIVERSITY OF UDINE. (2020). “Formal Analysis of MTProto 2.0 with ProVerif”. Disponível em: https://core.telegram.org/techfaq. Acesso em: 12 out. 2025.
UAS VISION. (2025). “Russia Controls Shahed Drones in Ukraine via Telegram Messenger”. Disponível em: https://www.uasvision.com/2025/05/28/russia-controls-shahed-drones-in-ukraine-via-telegram-messenger/. Acesso em: 12 out. 2025.